Okta
This article includes information on adding Okta as an integration to sync objects to Oblique. To use Okta as an identity provider to authenticate to Oblique, see Single sign-on.
When you connect an Okta tenant to Oblique, Oblique will automatically sync users, user attributes, and Okta groups from Okta to Oblique.
Oblique initially adds all resources in “Pull” mode, meaning that Oblique treats Okta as the source of truth and pulls information on these resources to Oblique. When you change the management mode of a resource, Oblique will automatically sync changes with Okta. For example, if you change a resource from “Pull” to “Push,” Oblique becomes the source of truth and pushes changes to Okta.
As you make changes in Okta, Oblique adds any new users and groups to Oblique, and archives any deleted users and groups in Oblique.
Supported options
Section titled “Supported options”Oblique integrates with Okta:
- As a source for users and user attributes
- As a source and destination for resources (Okta groups and Okta apps)
Supported resources
Section titled “Supported resources”- Okta groups
- Okta apps
Add Okta integration
Section titled “Add Okta integration”To add an Okta integration, you need to have an Okta API token.
To generate an Okta API token, in Okta’s Admin Console, navigate to Security > API, or go directly to https://$your-okta-domain.okta.com/admin/access/api/tokens:
- Select the Tokens tab.
- Select Create Token.
- Under What do you want your token to be named?, enter a name for the token.
- Under API calls made with this token must originate from, select “Any IP”.
- Select Create token.
- Reauthenticate to Okta.
- Copy the token value that is provided. It will not be shown again. When done, select OK, got it.
Read more about creating an API token in Okta’s documentation ↗.
- Navigate to the Integrations page.
- Select Add integration.
- Select Okta.
- Enter the Okta domain base URI, such as
https://example.okta.com, and API key, which starts with00. - Select Create integration.
Oblique will immediately start syncing users, user attributes, and Okta groups from Okta to Oblique.
Users can be filtered out of the sync through the integration settings.
Add Okta integration in read-only mode
Section titled “Add Okta integration in read-only mode”Oblique does not require write permissions to import users and groups from Okta, and will not modify your Okta environment until explicitly enabled to do so.
Optionally, to add an Okta integration to Oblique in read-only mode, you will need to create and use an API token for an Okta user with the desired limited set of permissions, such as the Okta Read-only Administrator role ↗.
To create a read-only Okta API token, you must:
- Create a new user in Okta
- Assign the user the appropriate role
- Authenticate as that user
- Generate an API token
Create a new user in Okta
Section titled “Create a new user in Okta”In Okta’s Admin Console, navigate to Directory > People:
- Select Add user.
- Fill in the information to create a new user account. This does not need to be a real person, and could be a service account or email alias.
- Optionally, if this is an account you will log into, like a service account, then under Password, select Set by Admin and enter a password. Keep this safe.
- Select Save.
Read more about manually creating a user in Okta’s documentation ↗.
Grant the new user a read-only admin role
Section titled “Grant the new user a read-only admin role”In Okta’s Admin Console, navigate to Security > Administrators:
- Select the Admins tab.
- Select Add administrator.
- Under Select admin, search for and select the user you added.
- In the Complete the assignment section, under Role, search for and select “Read-only Administrator”, or the desired role.
- Select Save Changes.
Read more about assigning admin roles in Okta’s documentation ↗.
Authenticate as the new user
Section titled “Authenticate as the new user”- If needed, log out of your Okta Admin Console. Select your username in the upper right of the Okta Admin Console, then select Sign out.
- From your Okta Admin Console tenant’s login screen, log in with the new user’s username and password.
Generate an API token for the new user
Section titled “Generate an API token for the new user”In your Okta Admin Console, navigate to Security > API:
- Select the Tokens tab.
- Select Create token.
- Under What do you want your token to be named?, enter a name for the token.
- Under API calls made with this token must originate from, select “Any IP”.
- Select Create token.
- Reauthenticate to Okta.
- Copy the token value that is provided. It will not be shown again. When done, select OK, got it.
Read more about creating API tokens in Okta’s documentation ↗.
You now have an Okta API token with the permissions of the Okta Read-only Administrator role.
Manage Okta groups
Section titled “Manage Okta groups”Manage existing Okta groups
Section titled “Manage existing Okta groups”Oblique can manage Okta groups and act as the source of truth for group membership. You configure this setting at the resource level.
This setting starts on by default and you can’t turn it off.
Create new Okta groups
Section titled “Create new Okta groups”Oblique can create Okta groups and act as the source of truth for group membership by creating new Okta groups for new team groups in Oblique. You configure this setting at the resource level.
This setting starts off by default.
To create new Okta groups for new team groups, you first need to enable this setting for the integration:
- Navigate to the Integrations page.
- Select the desired Okta integration.
- Select Settings.
- Toggle Create resources for new teams to On.
When you create a new team group in Oblique, Oblique will create a new Okta group with the same name in “Push” mode.
Manage Okta apps
Section titled “Manage Okta apps”Manage existing Okta apps
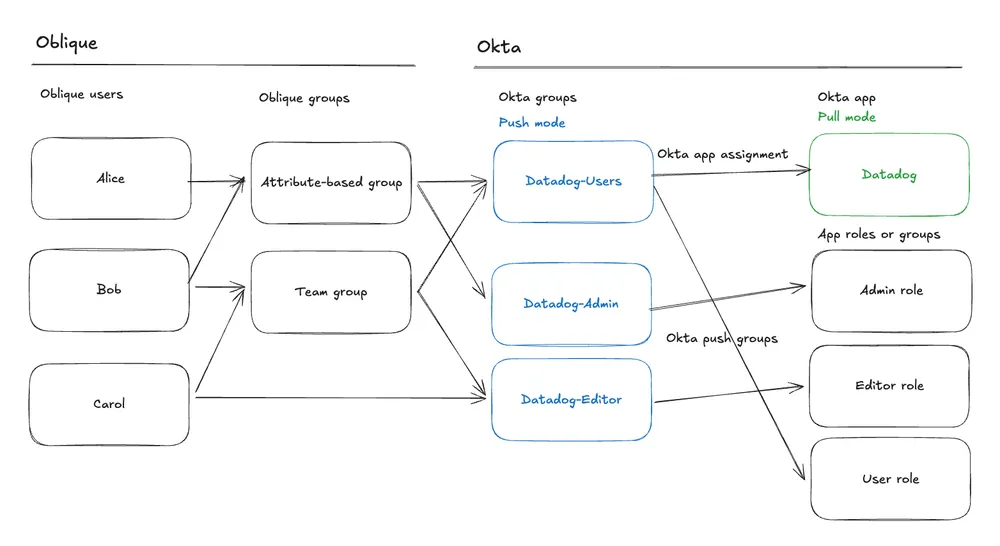
Section titled “Manage existing Okta apps”Oblique can manage Okta apps and act as the source of truth for app assignments. However, we don’t recommend this approach — most organizations with existing Okta setups prefer Oblique to push to Okta groups rather than directly to Okta apps. This is because Oblique currently cannot manage push groups assigned to Okta apps.
Instead, you can use Oblique to manage Okta groups, which then handle downstream access through Okta’s native capabilities. This works well if you have Okta push groups configured for your applications, so that you can push users into specific roles or groups within each app. Use listings to expose these roles or groups to users for self-service access requests.
The diagram illustrates this flow: Oblique users, attribute-based groups, or team groups are pushed to corresponding Okta groups. These Okta groups could be surfaced to users in Oblique using listings. From there, Okta handles app assignment (provisioning users in the app) and group push (syncing group membership to the app).
Push mode for Okta apps starts off by default. To enable push mode for Okta apps for your Oblique instance, contact support. Once enabled, you configure push mode at the resource level.
Sync Okta integration
Section titled “Sync Okta integration”You don’t need to do anything to sync the Okta integration. Oblique will automatically and continuously sync changes with Okta according to the sync frequency.
Remove Okta integration
Section titled “Remove Okta integration”To remove an Okta integration, from the integration’s detail page:
- Navigate to the Setings tab.
- At the bottom of the page, under Danger zone, next to Delete integration, select Delete….
- In the confirmation dialog, select Confirm.
This will immediately stop all syncing and remove all resources from the integration.